
Recently, I have developed few systems which require working with devices integrated with a network. Now the problem was that I was using open-source platforms for the development, but all the SDKs and guidelines for these devices are only available for proprietary platforms. The only thing that I was able to do in the opensource platforms was to login to the webserver inside the device with a browser.
Luckily, there was a web interface in these devices. So I’m going to explain the way I used it when the device is having a web interface.
Browser Dev Tools
In these situations, what I did was trace the packets which I sent with the browser interface. The Dev Tools of the browser is the easiest way to do the trace.
Authorization
Most of the devices have a username, password login interface to authorize the user into the device. Authorization technology of these devices can be anything. The tracing authorization method can be the hardest thing to do in your entire application.
What I did is I preserved the log in the network tab and just logged in to the device using the username and password provided. Preserving log can be important here because most of the time, once the username and password are provided, it might be redirected to another page and the network might be cleared.
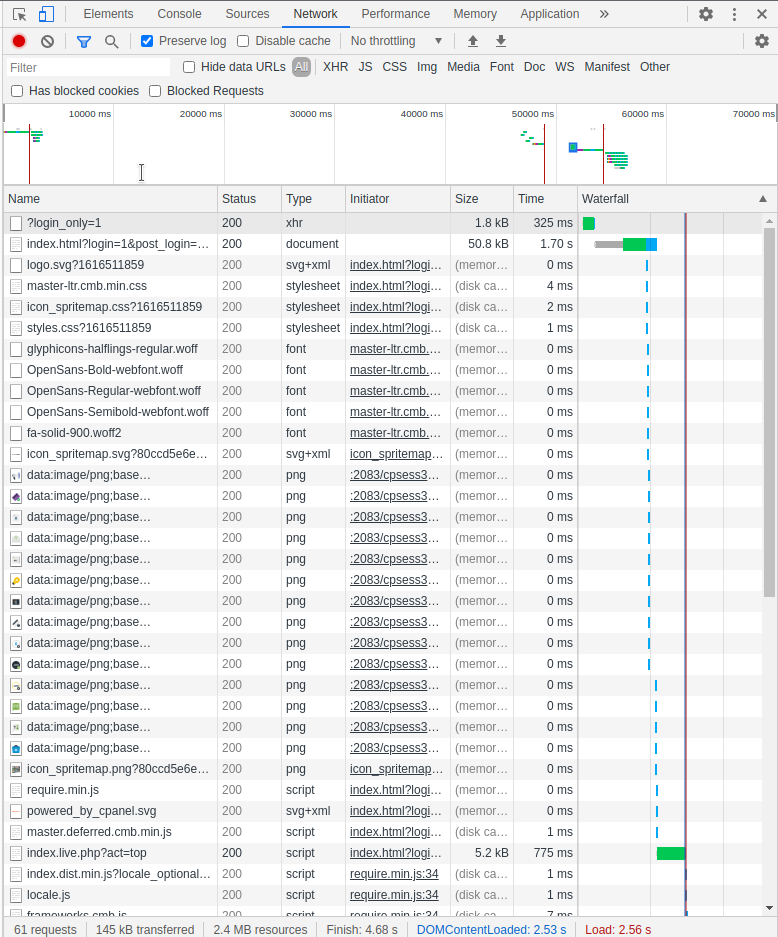
Now what I did was checking all the network requests in order to replicate the same request to get authorized to the device. In the system that I was developing, I simply recreated the exact request and the response is used in the rest of the requests.
If there are any hash generations involved in the login process, life will get uglier. In a situation like this, you have to check the sources of the website. Normally all kinds of hash generations are done by javascript codes. These codes should be downloaded to your browser before execution, so you are able to read these javascript files in the sources tab. You should be intelligent enough to track the exact javascript code which generates the hash and then you should recreate it in the system that you are designing.
Reading Data From the Device
Normally the web interface provided by the device itself can perform all the things that the device able to do. When I was tracing a reading operation, what I did was I first went to the webpage that the readings were showing. Now there can be two types of readings in this kind of situation. There can be either one-time readings or periodically updating readings. Either way, there should be a request to initiate the reading. That request should be traced and recreated first.
If the request is to read a one-time value, the value should most probably in the response to the request.
If the request is to get periodic values, there can be several ways to get the values. It can be a WebSocket or periodic request pattern etc. If the way is a WebSocket, you should create a WebSocket in your program and recreate the method. If this is a periodic request pattern, you should find the frequency of the request and recreate the exact pattern with a timer may be.
Writing to the Device
This is almost as same as the authorization trace. What you should do is update the values required via the web interface and recreate the requests as it is.
Session Timeout
This is a very important thing when doing a trace. What I did was I waited till the timeout period and checked the response for each request once the session is finished. And then I programmed the system to reauthorize if this response is received.
This should be done for both session timeout and manual logout.
Some devices have a way to refresh the session as well. So you have to find out what your device required and create the program.
So that’s it!
I hope you get an idea about how to work with a device with a network even if there’s no developers manual. Please comment or email if there are any suggestions.
